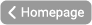
Security Incidents
In the Security Incidents section, you can see all IS incidents that have been reported in a table. You can also report an incident yourself, describing what happened, who is involved, and which assets are affected. In this way, information security officers can easily identify critical assets and their risks.
Instructions - Report and define security incident:
-
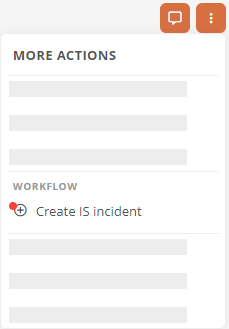
In the Security Incidents section, click More actions and then click Create IS incident:
OR
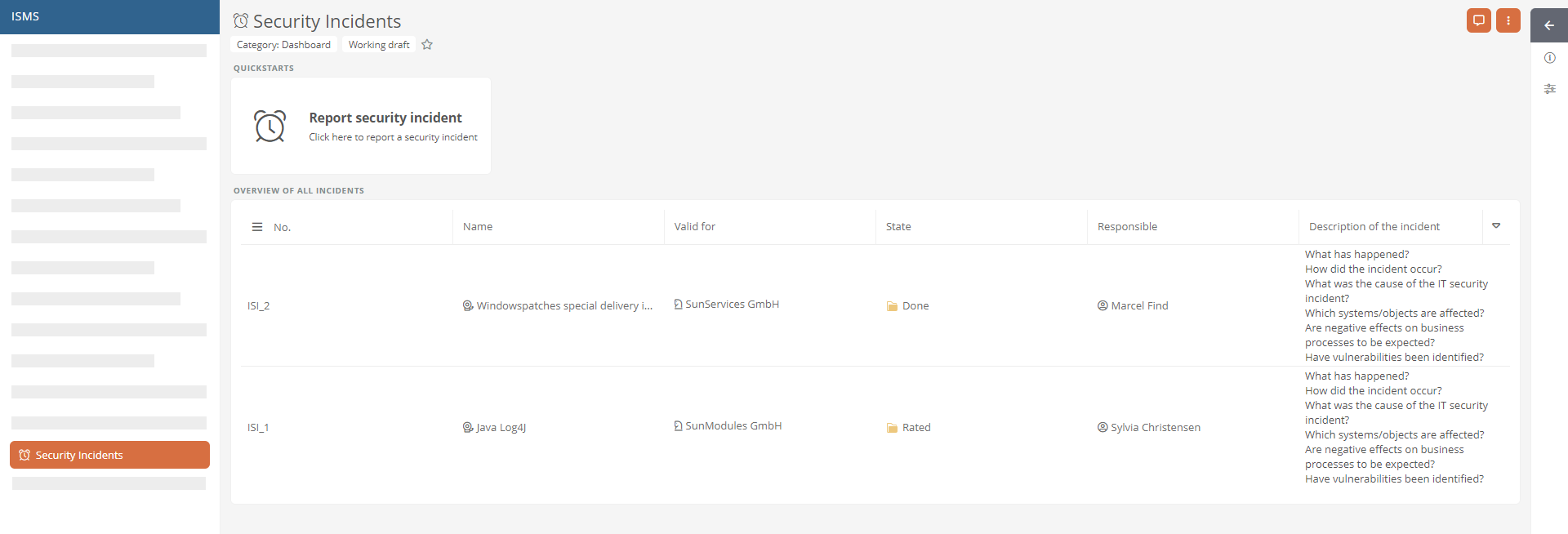
On the ISMS app homepage or in the Security Incidents section, click the Report security incident quickstart box:
-
Fill in the form. You can further define the security incident via the properties.
Note: The form fields marked with * are required.
| Property | Description |
|---|---|
| General | |
| Description | Enter a name for the security incident here. |
| Valid for | Reference here a scope in which the security incident is valid. |
| Description of IT security incident | Describe the security incident here. |
| State | Here you can select the state of the security incident. |
| Reporter of the incident | Enter the reporter of the security incident here. |
| Mandatory to be reported to the German Federal Office for Information Security | Specify here whether the security incident must be reported to the German Federal Office for Information Security. |
| Is IT security incident | Specify here whether the security incident affects IT. |
| Attachments | Here you can attach a file. |
| ISMS | |
| Reaction/counter measure | Describe here the reaction or counter measure that will be taken. |
| Security incident | Describe the security incidents here. |
| Responsible | Reference a user or employee responsible for the security incident here. |
| Similar IS incidents | Reference similar security incidents here. |
| Occurrence of IT security incident | Specify here when the IT security incident occurred. |
| Detection of IT security incident | Indicate here when it was recognized that this was an IT security incident. |
| Notification of IT security incident | Specify here when the IT security incident was reported. |
| Completion of IT security incident | Indicate here when the IT security incident was closed. |
| Intentional act | Here you can select to what extent it is an intentional act. |
| Nature of the intentional act | Here you can select or create the type of intentional action. |
| Random security incident | If a random security incident has occurred, you can select or create the type of random security incident here. |
| Error as security incident | Here you can select the error that led to the security incident. |
| Unknown type of security incident | If the security incident does not belong to a specific type, you can describe it here. |
| Affected items | Here you specify the asset that is affected by the security incident. |
| Loss of confidentiality (weighting) | Here you rate the loss of confidentiality on a scale. |
| Loss of confidentiality (impact) | Here you describe the impact of the loss of confidentiality. |
| Loss confidentiality (cost) | Here you quantify the cost of losing confidentiality. |
| Loss of integrity (weighting) | Here you rate the loss of integrity on a scale. |
| Loss of integrity (impact) | Here you describe the impact of the loss of integrity. |
| Loss of integrity (cost) | Here you quantify the cost of losing integrity. |
| Loss of availability (weighting) | Here you rate the loss of availability on a scale. |
| Loss of availability (impact) | Here you describe the availability of the loss of integrity. |
| Loss of availability (cost) | Here you quantify the cost of losing availability. |
| Destruction (weighting) | Here you rate how severe the destruction is on a scale. |
| Destruction (impact) | Here you describe the impact of the destruction. |
| Destruction (cost) | Here you quantify the cost of destruction. |
| Cost overall (weighting) | Here you rate how high the costs are proportionally on a scale. |
| Cost overall (impact) | Here you describe the impact of the total cost. |
| Total cost | Here you quantify the total cost. |
|
Start of treatment |
Here you indicate when you will start handling the security incident. |
| Coping of IT security incident | Here you specify when the IT security incident was managed. |
| End of impact | Here you specify since when there are no more effects. |
| Termination of the investigation | Here you specify when the investigation was completed. |
| Originator | Select here who caused the incident. |
| Presumable motivation of originator | Describe here the motivation of the originator. |
| Summary rating | Select here whether the overall significance of the security incident is low or high. |
| Summary importance (individual) | Describe the significance of the security incident here. |
| Contacted persons/institutions | Select here which persons or institutions are to be notified. |
| Other attributes | |
| Treatment measures | Here you can reference tasks to handle the security incident. |